�@�B�e��
���ں����N�����_�A���s�N�������A�ϱo�j�a�U�ӷU����Internet�o�����μs�x�����������C�]���p�����ϥΪ̳z�L���ں����q�T�A�Ӥ��ξ�߶ǰe���H���ʥ]�Q�I���B���_�A�N��o�۷����n�C�]���o�ǫʥ]���e�i��A��ID�A�H�Υd���X�����n���ӤH��ơC
�ƹ�W�A�o�X�~�Ӻ��ں����W���w���зǦ��ܦh�C�Ҧp:RFC1508�M1509�ҳW�w��GSSAPI(Generic Security Service Application Program
Interface)�ATelnet�AFTP�MHTTP���i�H�ϥ�;���ں����u�{�p��(Internet
Engineering Task Force; IETF)��PSRG�p�թҭq�w��PEM�зǥi�H�F��E-mail���w���ʡA�Ӻ����̵ۦW��E-mail�w���n��h�OP. Zimmermann��PGP(Pretty Good Privacy);��L�pEIT��S-HTTP(Secure HTTP)�ANetscape��SSL(Secure
Sockets Layer)�AMicrosoft��PCT�H�ΤW�����Ϊ�GSSAPI���i�إ�HTTP���w������AVisa��SET(Secure Electronic Transfer)�h��F��w�����q�l�Ӱ�(Electric Commerce)�C�o�Ǥ��O��ܼh(Session
Layer)�����μh(Application Layer)�W���w������A�ϥΪ̥����ϥαM�ݪ��q�T��w�A�ίS�w�t�Ӫ����~�C
�ҥH�|���o�˪����D�A�i�H�����OTCP/IP�S���סAIP���Y�����ӷ�(Source)�A�ت�(Destination)��}�A�˸����(Payload)�A��TCP�u�t�d�N�H�����Φ��ʥ]�A�Y�ʥ]TCP�A���e�A�ҥHTCP/IP�ڥ��S���w���ʥi���A�ϥΤ@��Sniffing�n��u��A�Y�i�@���A�M�a�ݨ�o�ǫH���C
���F�T�O�b����IP�����W�֦��w�����p�K�q�H�A�]���F��X���P�зǤΤ��P�t�Ӳ��~�A IETF�ۤ�q�w�F�@�M�}��зǺ����w����wIPSec (IP Security)�C�N�K�X�N���Φb�����h�A�H���Ѷǰe�B�����ݰ���ƪ�����(Authentication)�B�����(Integrity)�B�s������(Access
Control)�B�H�ξ��K��(Confidentiality)���w���A�ȡC���h�����Ψ�]�i�H�����ζ����a�ϥγo�Ǧw���A�ȡC
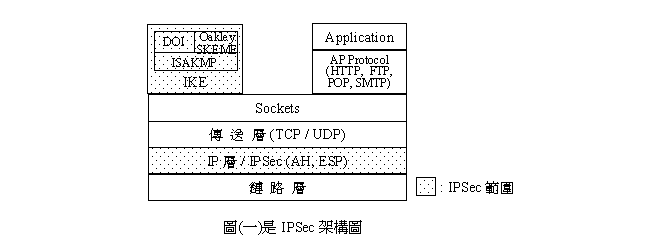
IPSec�O�]�p�ӹF������h���ݹ�ݦw���q�T���ĤT�h��w�A���D�n���[�c�OIP�{�����Y(Authentication
Header; AH)�H��IP�ʸ˦w���˸�(Encapsulating
Security Payload; ESP)�CIP AH���Ѹ�ƪ�����ʩM�{�ҡA�����]�A���K�ʡA��IP ESP��h�W�u���Ѿ��K�ʡA���]�i�bESP Header���q�w�A�����t��k�μҦ��ӽT�O��ƪ�����ʨû{�ҡAIP AH�MIP ESP�i�H���}�ϥΩΤ@�_�ϥΡC���㪺IPSec�����]�AIP AH�MESP���ҨϥΪ��_���洫�M�z�A�]�N�O�w���s��(Security Assocication; SA)�M���_�zIKE(Internet Key Exchange)�A��(�@)�OIPSec�[�c�ϡA�䤤DOI(Domain of interpretation)�O���F����L��w�i�H�ϥ�ISAKMP�ӭq�w��Framework�A��(�@)���ڭ̫ܲM�����DIPSec�MIKE�ҧ�t������C
���媺�ĤG�����N����IP AH�A�ĤT���������e�OIP
ESP�A�ĥ|�����ԭz�w���s��SA���[���A�Ĥ������h�O�H�@�ӹ�ڪ��Ҥl�ӻ���IP AH�MIP ESP��ڹB�@�����ΡA�Ĥ���������SKIP��ISAKMP/Qakley���IETF�ҰѦҪ����_�z��w�CISAKMP/Oakley�����u�ʥB��䴩���h����w�A�w�Q�אּIPv6��IPSec���_�z��w�C�̫�@�����h�O�HISPec�����רӬݥ��bVPN�W�����ΡA�þ�z�C�X�ثeVPN�ŦXIPSec�зǪ��ӥβ��~�C
���M�w��IP�h���w������|����L��IP
Tunneling�N�A�Ҧp��ө�PPP�ӵo�i��PPIP(Point-to-Point
Tunneling Protocol)�A�o�O��Microsoft�MAscend�Ҧ@�P���X�A�i�䴩IP/IPX/NetBEUI�A�䴩���t�ӫh��Nortel�A3COM�C�t�~L2TP(Layer 2 Tunneling Protocol)�h�O�ĦX�FPPTP�MCisco��L2F(Layer
2 Forwarding)�A�D�n���t�Ӧ�Nortel�MIBM�C
����D�n����IFTF�Ҩ�w���}��з�IPSec�A�]�������X���P��VPN�t�ΦӹF��w���a�������s�ت��C
�G�BIP AH�榡
IP
AH���ѻ{���θ˸���ƪ�����ʡA�����t���K�ʡC�ѩ����Ѿ��K�ʡA�ҥH�����K�X����~��X���x�譭��A�G���P����a�����ں����ϥΡC
IP
AH�ϥλݭn128�줸���_��MD5(Message
Digest 5)�p��X��Ӹ�ƪ������ƭ�(��:����V����Ƥ]�i�ϥ�SHA-1 (Secure Hash Algorithm 1))�A�ϱo������(���D���_���H)�]�i�H����B�p��O�_�ϥάۦP���K�_�H�ˬd��ƬO�_���T����A�Y�ˬd���ūh�N���ʥ]���C�̾�IPSec�W�w�AIPv6�C���D�������ണ�ѱK�_����128�줸��MD5�A�өҦ�IPv4�]���ŧi��䴩����AH�\��C
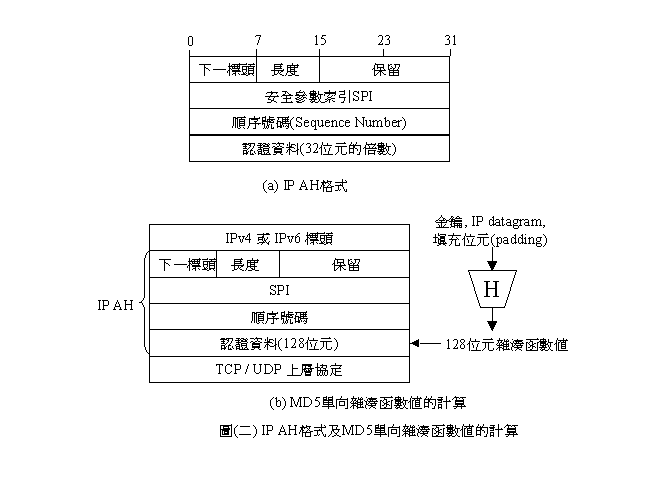
IP
AH���榡�p��(�G).a�ҥܡA�䤤�C����쪺�N�q���O�ԭz�p�U:Next Header����8�Ӧ줸�A�o�Ӽ��Y�O�w�qAH�᭱��ƪ�����;��ƪ������]�O8�Ӧ줸�A���M�w�{�Ҹ����쪺���סA�t�~�٦�16�ӫO�d�줸�����Ӥ��ΡC�w���ѼƯ���(Security Parameter Index; SPI)�O����32�Ӧ줸�������üơA�M�w�w���s��SA�����e�A�Ҧp��0���O���ܨS��SA�A��1~255�h�O�O�d�ȡC�bSPI�᭱���O���Ǹ��X���(Sequence Number Field)�A�[�J�o�Ӹ��X�i����e����(Replay
Attack)�C�̫�@�����O�{�Ҹ�ƪ��O�i�ܪ�(32�줸������)�C��(�G).b��ܤF�ϥΫH���K�n���MD5�A������128�줸�������ƭȡC�q�Ϥ��]�i�ݥX��IPv4��IPv6�Ө��CIP AH �O�bIP���Y�MTCP(��UDP)�����C
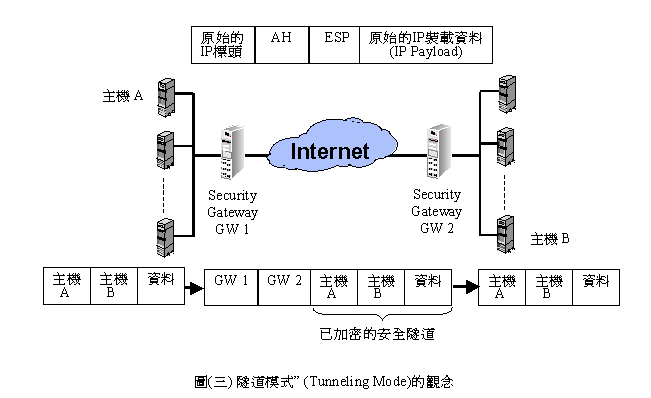
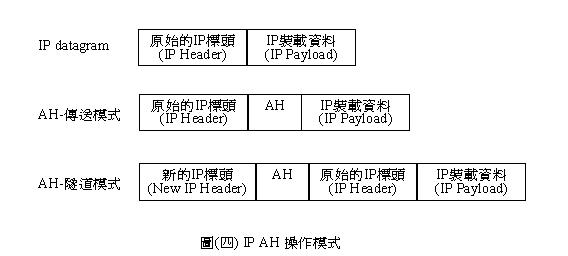
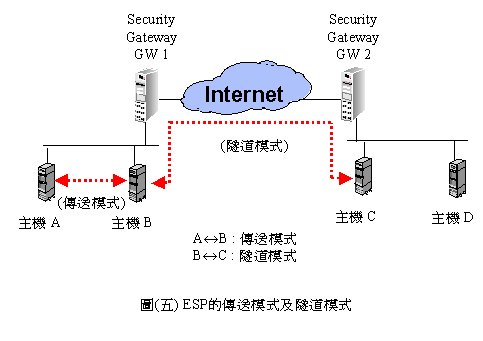
�bIPSec�����ެOIP AH��IP ESP�A������ؤ��P���ާ@�Ҧ��A�G�D�Ҧ�(Tunneling Mode)�ζǰe�Ҧ�(Transport Mode)�C�٨S����IP AH��ؼҦ��e�A�ڭ̥��ι�(�T)�Ӹ����̱`�ϥΪ��N
���G�D�Ҧ��� ���[���A���IP
datagram�Q�]�b�s��datagram���C��(�|).a~c���O����l��IP datagram �A AH�ǰe�Ҧ��� AH�G�D�Ҧ��A���AH�G�D�Ҧ��Ө��A�̫ᥦ�u�O�@�ӷs��IP datagram�Ӥw�C
�T�BIP ESP�榡
IP
ESP�зǴy�z�p��[�KIP���˸����(Payload)
�A�[�K���d��i�H�O���IP Datagram�Ϊ̥u�O�W�hTCP�AUDP�A��ICMP���(�����M�w�b�ϥ��G�D�Ҧ��ζǰe�Ҧ�)�CIP ESP�ҨϥΪ��O�K�N�O�ƾګO�K�з�(Data Encryption Standard; DES)�άOTriple-DES�A�Ҧ��h�O�[�K�϶���(Cipher
Block Chain ; CBC)�C���F�[�K�H�~�AIP ESP�]�����Φb�{�ҡA����ʡA�H�Ψ���e�����C
IP
ESP���G�D�Ҧ��ζǰe�Ҧ��U�����u�I�C�G�D�Ҧ��i�H�b���Security Gateway���إߤ@�Ӧw�� ���G�D���A�p��(��)�ҥܡA�g�ѳo���Gateway
Proxy���ǰe���b�o���G�D���i��C���[�ǰe�Ҧ��[�K���������֡A�S���B�~��IP���Y�A�G�u�@�IJv���ΡC
�o��ؼҦ����ާ@�Բӻ����p�U:
1.�ǰe�Ҧ�:
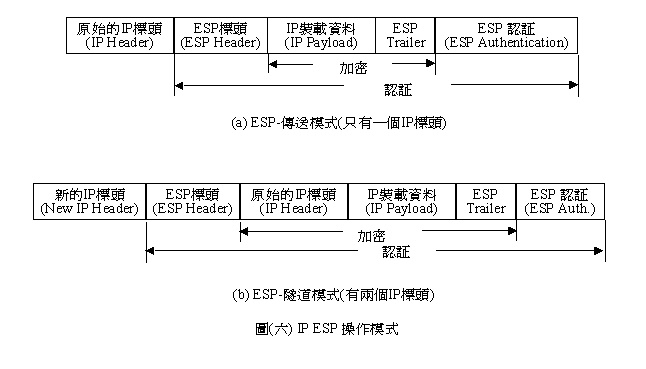
��(��).a��IP ESP���ǰe�Ҧ��AESP���Y�����[�b���ǰe����ƫe�A�o�ؼҦ��i�`���W�e�C�]��IP���Y���ݥ[�K�A�ҥH�����G�D�Ҧ��A�@�ӫʥ]�������IP���Y�C
�����NIP�˸���ƨϥ�ESP�ʸ˰_��(ESP Header�M ESP
Trailer)�C�ǰe�ݧQ�ΨϥΪ�ID�M�ت��ݦ�}�H�o��SA����(�U�@�`�|�[�H����)�A�M��Υ[�K�t��k(DES��Triple-DES)�[�K�ǰe����ơC�����ݦ���ESP�ʸ˪��ʥ]�ɪ����B�zIP���D(�]���S���[�K)�A�M��qESP Header����SPI�ȥH�o��۹諸SA�A�A�Q��SA���w�����ҩҭq���ѱK��ƸѥX�ҥ[�K����ơC
��ǰe�Ҧ��Ө��A�ѱK���H�N�O�ت���}�ݪ��ϥΪ̡C���O�w��Firewall�A Gateway
Proxy�Ө��A�ϥ��G�D�Ҧ��h�����X�A�A�]���L�̨ä��O��l���e�A���ݡC
2.�G�D�Ҧ�
��(��).b�O�G�D�Ҧ����[�c�ϡA�G�D�Ҧ��i�H²��a�Τ@�y�ܨӻ��� ��IP-in-IP���C�����ϥ�SA�������T���NIP���ʥ]�[�K(�tIP���Y)�A���U�Ӧb�e���[�WESP Header�C�M��Prepend�s��IP���Y�C�����ݦ���ESP�ʥ]��A�ϥ�ESP
Header���e����SPI�ȨM�wSA�A�M��ѥXESP Header�᪺�˸���ơA�N�i�H���^��l��IP���Y�P�ʥ]�A�i�H�~��a���U�ǡC
��(�C)�OESP Header��ESP
Trailer�����e�A ESP Header�]�t�FSPI�ȡA�ҩl�ƦV�qIV�A�ζ��Ǹ��X��쵥�A�䤤���Ǹ��X�i����e�����C
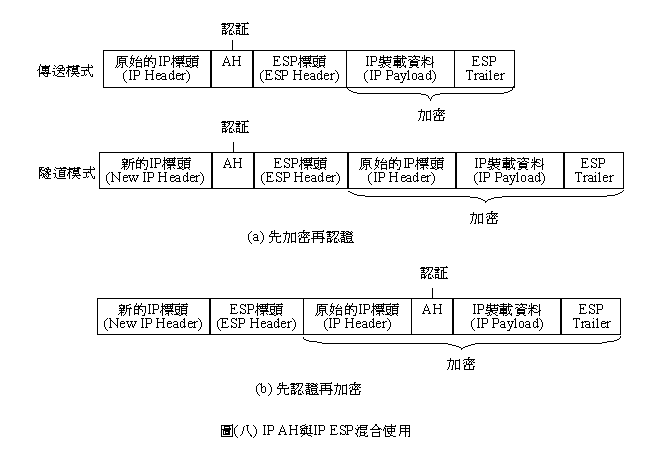
3.IP AH�PIP ESP�V�X�ϥ�
IP
AH�PIP ESP�i�H�W�ߩΤ��}�ϥΡC��(�K).a�O���[�K�A�{�ҡA��ƻ{�Ҥ��e�@�[�K�C��(�K).b�h�O���{�ҦA�[�K�A�����n�B�O��{�Ҹ�Ƥ]���[�K�A�]���S���H�i�H��ʻ{�Ҹ�ơC
�b���Ч��U�@�`�w���s��SA���[������A�ڭ̱N�|�H�@�ӹ�ڪ��Ҥl�ӻ���IPSec��IP Header �AIP AH�A IP ESP�A SPI�����ާ@���ΡC
�Ĥ@�N��IPSec������1995�~���X(rfc 1825, rfc 1826, rfc 1827)�A������_���洫�M�z�å��w�q�A�ұj�ժ����e�O�ʥ]�ഫ���榡�C�������w���W���~�ӧﭲ�W�c�A�ثe�̷s��IPSec�����w��1998�~���X(rfc 2401, rfc 2402, rfc 2406)�A�W�[�۰ʪ��_�洫�B��s�F�ʥ]�ഫ���榡�A�ϱoIPSec�[�c�U�ͧ���C
�|�B�w���s��SA
�bIPSec�зǤ��̭��n�����شN�OSA�A���w�q�F�@�Ӧw�������������A�o�����Ҫ����e�]�t�FIP�ʥ]�[�K�A�ѱK�A�M�{�Ҫ������T���A�ԭz�p�U:
l
�K�X�\��:���ѥ[�K�λ{�ҩΨ�̦P�ɡC
l
�K�X�t��k:�Ҧp�[/�ѱK�ϥ�DES(�� Triple-DES)�{�Ҩϥ�MD5 (��SHA-1)�C
l
�K�X�t��k���ҨϥΪ����_�A���_���ͩR�g�����C
l
�O�_���ҩl�ƦV�q�C
l
SA���ͩR�g��
SA�i�H�ϥΦw���ѼƯ���SPI(32�줸)�Ӵy�z�A�]�N�O�@��SPI�ȨM�w�@�ӯS�w��SA�A�ӥD����IP��}�PSPI�h�w�q�F�ߤ@��SA�C�Ҧp�D��A�i�H�q���D��B SPI�Ȭ�1000�A���Ҭ۹諸SA���ҡA�K�X�\�ର���u�[�K�A��DES�A���_��0x1234567890abcdef(����64�줸�A�䤤8�Ӧ줸���P�줸)�C�ҥH�D��A�N�i�H�ǥ�SPI 1000���Ȩӥ[�K������ơA�M��ǰe��D��B�C��B����ʥ]��Q�ΥD��A�MSPI���ȴN�i�H�M�w�XSA�ӸѱK���^��l��ơC
�q�W�����ԭz�i�H�o�{SA�O��V��(A®B)�A���O��D��A�P�D��B�o��ӭn�إߦw���q�T���D���Ө��h�ݭn���SA�A�C�@��V�@�ӡA(A®B)�M(B®A)�C
���~SA���ϥΦ������J�覡�A�D���ɦV��J�覡(Host-Oriented Keying)�P�ϥΪ̾ɦV��J���(User-Oriented Keying)�C�e�̬O���Ҽ{�ϥΪ̡A�q�P�@�Өt�Ωҵo�X���ʥ]�A���ϥάۦP�����_�A�ӫ�̫h�O�H�ϥΪ̬��Ҷq�A���\�ϥΪ̦����P�����_�C�Ҧp:�P�@�ϥΪ̦��h����_�ΩP���A�ȡA�pFTP�PTelnet�ϥΤ��P�����_�C
���B�@��IPSec����ڨҤl
�G~�|�`�w���ФFIPSec���[�c�AIP AH�A IP ESP�A SA�A SPI���C�{�b�ڭ̱N�o�ǥ�����b�@�_�H��ڪ��Ҥl�ӥ[�H�����C
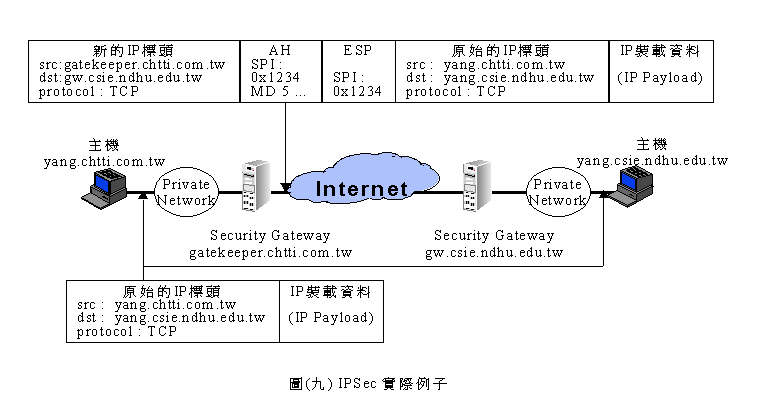
EXAMPLE:���]���@�ӥD��yang.chtti.com.tw���ǥ�IPSec�w������N�㦳�[�K�λ{�Ҫ�TCP�ʥ]�e��t�@���D��yang.csie.ndhu.edu.tw�C���Ʊ楦��gateway gatekeeper.chtti.com.tw�వ�[�K�A�{�����u�@�A�ӹ�誺gateway gw.csie.ndhu.edu.tw��ѱK�o�ǫʥ]�û{���A�ϥΪ�SPI�ѼƭȰ��]�O0x1234�O���V�j�a�ƥ��P�N���w���s��SA�C
��(�E)�O�o��IPSec�Ҥl�������ܷN�ϡA���D��yang.chtti.com.tw�Ұe���ʥ]�쥦��gateway�ɡA gateway�[�K�ʥ]�å[�JESP Header�A�M��[�JAH�M�s��IP���Y�A�䤤�Hgateway����}gatekeeper.chtti.com.tw���@�s���ӷ���}�A�åHgw.csie.ndhu.edu.tw���@�s���ت��ݦ�}�A�̫�p�������ƭȨå[�bAH���C
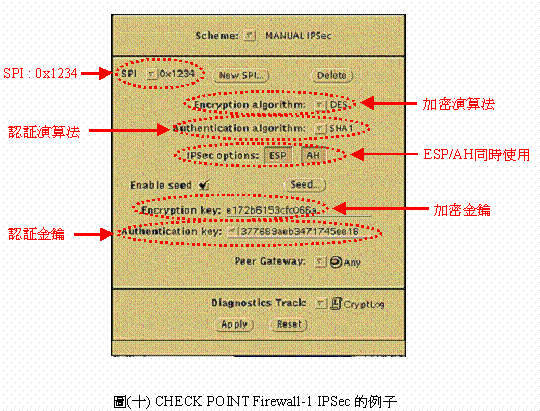
��(�Q)�OCHECK POINT Firewall-1(CHEK POINT�bFirewall���������v��44%)���Ҥl�AFirewall-1���ܦn���H���ɭ�(GUI)�A�q�Ϥ��i�H�M���ݥX�ϥΤFAH�MESP�A�{�ҥΪ���V�����Ƭ�SHA-1�A�[�K�t��k��DES�A�P�ɤ]�i�ݨ�[�K�λ{�Ҫ����_�ASPI���ƭȬ�0x1234�C
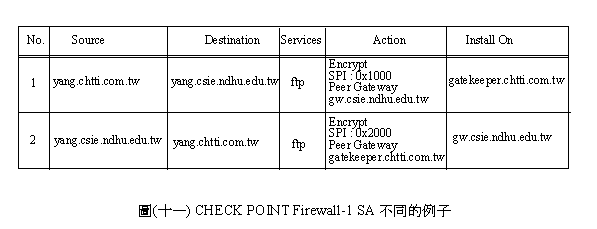
�ѩ�w���s��SA�i�H�O���P���A�ҥH�ڭ̤]�i�H�bCHECK POINT Firewall-1����Security Policy�[�J�U������W�h(rule)�A�p��(�Q�@)�ҥܡC�]���ϥΪ�SPI�Ȥ��@�ˡA�qyang.chtti.com.tw��yang.csie.ndhu.edu.tw����V�O�ϥ�SPI
0x1000�A�Ϥ�V�h�O�ϥ�SPI 0x2000�A�o��x�D��������FTP�ɨϥΪ��t��k����_�i�H�O���P���C
���BIPSce�����_�z��k
�bIP AH�MIP ESP���ҥΨ쪺�{�һP�[�K���_�A�p��洫�P�z�O!�@����_�O�_�@���ϥΩO!�o�ǰ��D���|�����ΡA�o�ǰ��D��IPSec�Ө��O�D�`���n�����D�C
�p�G�O�X�x�D���A�i�H�ΤH�u���覡�ӥ洫���_�A�Ҧp���q�ܩ�E-mail�A���O�D���ƥؤ@�h�A�Ϊ̬O�D����Ʊ`���A�o�ɫJ�N�ݭn�@�M�w���B��������w�Ӱ��o��Ʊ��F�C
�ثe�D�n�����_�z��w���ѦҳW�d��:(1)SKIP(Simple Key-management for IP)(2)ISAKMP/Oakley(Internet
Security Association Key Management Protocol /Oakley )�C�W�z��ؤ�k���i���ΦbIPv4�PIPv6���ASKIP����²��A��ISAKMP/Oakley�h�i�H���Ω���h����w�C�ƹ�W�AIP�h�����_�洫��w�|��Photuris�MSKEME���C
1.SKIP:
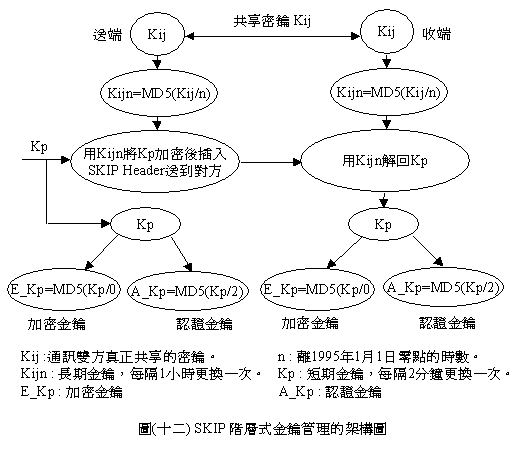
SKIP�O��Sun Microsystem�ҵo�i�A�ئ��T�ت���:Sun�A TIK�A�MELVIS+SKIP�CSKIP���_�z���[���O���h�������_�z�A�p��(�Q�G)�ҥܡC�q�T������u���@�ɪ��K�_�OKij(�o�O�Q��Diffie
Hellman�����}���_��ӹF��@�ɪ�)�C���F�w�����Ҷq�A���}���_���ܾ��Һz����(Certificate Authority;CA)�ӽо��ҡC�]��IPSec���ϥΤ]�ݭn�C�@��a�����}���_��¦�س](Public Key Infrastructure;PKI)�Ӱt�X�C
�ϥ�Kij���ɦӱoKijn=MD5(Kij/n)�A�䤤n�O�{�b�ɶ��Z��1995�~1��1��s�I���ɼơAKijn�O�@�Ӫ������_(�C�j1�p�ɧ@��)�A�Q��Kijn�o����_�N�u�����_Kp(�C�j2�����@��)�[�K�ᴡ�JSKIP Header�e����C�����ݦ����Q��Kijn�Ѧ^Kp�C���U������ϥ�E_Kp=MD5(Kp/0)��A_Kp=MD5(Kp/2)�ɥX�[�K���_E_Kp�M�{�Ҫ��_A_Kp�C�ѩ���_���ɹL�{�O�@�h�@�h���A�]SKIP�٤������h�������_�z�[�c�C
�ڭ̤@�˨ϥβĤ��`���Ҥl:�����D��yang.chtti.com.tw���P�D��yang.csie.ndhu.edu.tw�Ұʳq�T���A�ӰQ��SKIP��w�A��(�Q�T)�OSKIP�ʥ]���e���y�z�C
SKIP����PISAKMP��X�Ҷq�A�����ѤF�C�]��IPv6�w�M�w�ϥ�ISAKMP�POakley���_�洫���X�֨�w�A�]�N�OISAKMP/Oakley(�{�w�٧@IKE;Internet Key Exchange)�C�ҥHSKIP�ëDIPSec�j��W�w�����_�z��k�C
2.ISAKMP/Qakley(IKE):
Oakley���_�洫��w�O�ѨȧQ�ᨺ�j�ǩҴ��X�A���PSEKME���۷��h���@�P����(��:SEKME�h�OPhoturis������)�C
ISAKMP����Ӿާ@���q�C�Ĥ@���q���A�������@�Ǧw���ݩʸg�L��ӡA�ò��ͤ@�Ǫ��_�A�K���C�o�Ǥ��e�c���Ĥ@��SA�A�@��٧@ISAKMP SA�A�PIPSec SA���@�˪��O���O���V���C�ĤG���q�h�O�HISAKMP SA���w�����Ҩӫإ�AH��ESP��SA�C
IKE�h�OISAKMP�ϥ�Oakley���@�ǼҦ��MSKEME�ֳtrekey���[���X�֦Ӧ��A����(1)Main Mode (2)Aggressive Mode (3)Quick
Mode(4)New group mode���|�ؼҦ��C
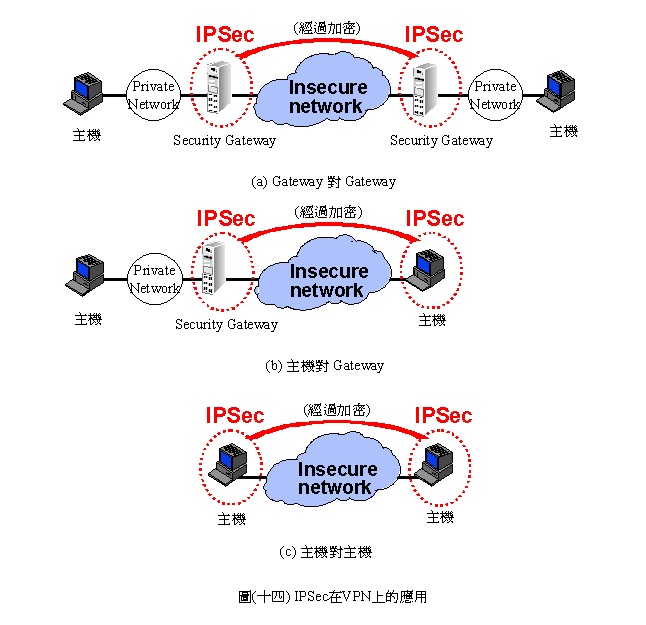
�C�BIPSec�bVPN�W������(�N����)
�b�F��IPSec��w���u�@��z��A�ڭ̨Ӭݥ����P���γ��X�A�ȱo�`�N���O�b�����h���Ѧw������A�����μh�Ө��O�����z�q��(trarsparent)�CIPSec�i�H�˳]�bgateway�ΥD���W�A�άO��̦P�ɡA�YIPSec�˦bgateway�W�A�h�i�b���w����Internet�W���Ѥ@�Ӧw�����q�D�A�Y�O�˦b�D���A�h�ണ�ѥD���ݹ�ݪ��w���ʡC��(�Q�|).a~c���O�Ogateway��gateway�A�D����gateway�A�D����D���T�إi����Ϊ��p�C
��(�@)�Z�X�ŦXIPSec���ӥ�VPN���~�A�@�����媺�����C
�ѦҸ��:
1.V. Ahuja�A��Secure Commerce on the Internet���AAP Proffesional�A1998.
2.L.J. Hughes��ۡA�s�q��Ķ�A��Internet�w���N������պ�1996.
3.1998��VPN�N�P�����Ͷլ�Q�|���A1998.
4.Internet Rosurces:
http://www.ietf.org/thml.charters/ipsec-charter.html
http://firewall.sysware.com.tw/faq/vpn/ipsec.html
http://firewall.sysware.com.tw/faq/vpn/SKIP.html
http://conway.cba.ufl.edu/ism6222/Ipsec.html
http://www.hsc.fr/veille/papier/papier.html.en

��(�@):�ŦXIPSec��VPN���~
|
���� |
���~�P��� |
���_�z |
���� |
���~�P��� |
���_�z |
|
1 |
Checkpoint |
SKIP |
8 |
Raptor system Inc. |
ISAKMP/Oakley |
|
2 |
Cisco systems Inc. |
ISAKMP/Oakley |
9 |
Secure Computing |
��� |
|
3 |
Cycon technologies |
��� |
10 |
Securicor 3Net
Ltd. |
��� |
|
4 |
IBM |
��� |
11 |
Sun Microsystems I |
SKIP |
|
5 |
IRE Inc. |
ISAKMP/Oakley |
12 |
Timestep corp. |
ISAKMP/Oakley |
|
6 |
NSC(Net. Sys.
Corp.) |
Proprietary
dynamic |
13 |
TIS(Trusted Info.
Sys. ) |
ISAKMP/Oakley |
|
7 |
Radguard Ltd. |
ISAKMP/Oakley |
14 |
VPNet |
SKIP |